If you’re a business owner, then it’s important that you understand all the security measures available to protect your data and other sensitive information. One of these measures is IP whitelisting, which is a way of allowing only certain IP addresses to access your network. Understanding what IP whitelisting is and how it works can help you keep your business secure.
What is IP Whitelisting?
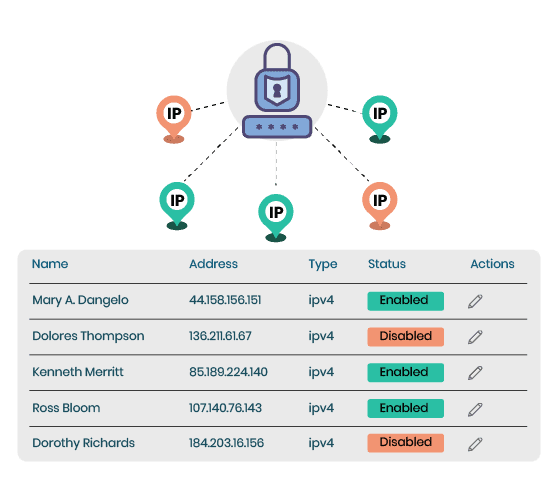
IP whitelisting is a security measure that allows only certain computers or networks to access a specific server or application. This means that if an unauthorized user attempts to access your server from an unapproved IP address, they will be denied access.
This helps to prevent malicious attacks from outside sources and ensures that only the people you trust are able to gain access.
IP whitelisting is an effective way to protect against malicious actors because it prevents them from gaining access to your data without having the proper credentials.
Additionally, it can help prevent denial-of-service attacks, which are when a malicious actor attempts to overwhelm a system by flooding it with requests. By limiting which IP addresses are allowed in, you can reduce the number of requests coming in and therefore make it more difficult for malicious actors to cause disruptions.
Why Use IP Whitelisting?
The biggest benefit of using an IP whitelist is improved security. By limiting access to only specific trusted devices and networks, you can greatly reduce the risk of unauthorized users gaining access to your resources.
Additionally, since all other devices are automatically blocked without any input from you, it eliminates the risk of human error when maintaining security protocols.
It also eliminates the need for more time-consuming manual authentication methods such as two-factor authentication (2FA).
It’s also important to note that there are certain limitations when using an IP whitelist—for example, if a device on the list has its address changed (e.g., due to a DHCP reset), then it won’t be able to access the protected resource until its new address is added back into the list. As such, you’ll need to be sure that any device on your allow list has a static address if possible so that it doesn’t accidentally get locked out due to an unexpected address change.
How Does IP Whitelisting Work?
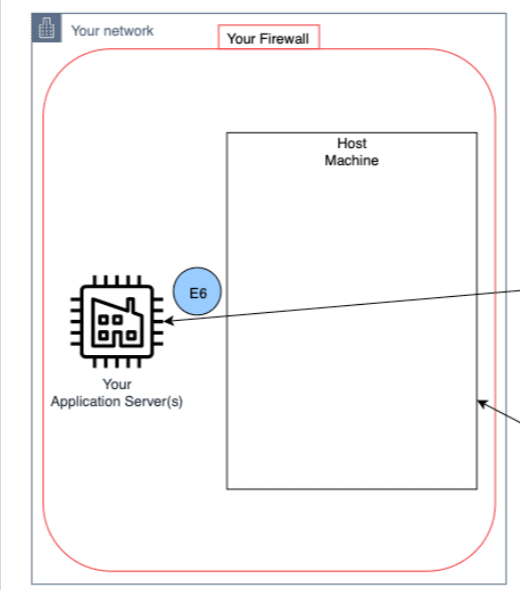
The basic idea behind IP whitelisting is that you can create a list of approved IP addresses (or ranges of addresses) that will be allowed access to a given network or website. Any other attempts at accessing the network will be blocked from reaching their destination.
This ensures that only trusted devices and users are able to gain access and keeps malicious actors out of your system.
Another way in which this process can be used is for email authentication purposes. Email providers like Gmail and Yahoo use whitelists as part of their spam filters.
When emails are sent from an unknown source, they are checked against the provider’s whitelist before they can reach their intended recipient. This allows legitimate emails to go through while blocking spam emails from ever reaching your inbox.
The process works by checking each incoming connection against the list of approved IP addresses before allowing them through. If the connection comes from an address that isn’t on the list, then it will be blocked automatically.
This makes it easier for websites to protect themselves against potential attacks while still allowing legitimate users in without too much hassle.
Limitations of Using an IP Whitelist
One major limitation of using an IP whitelist is that it may limit your ability to take advantage of certain features offered by third-party services such as analytics tools or marketing platforms.
Since these services often require accessing data from multiple sources, they may be unable to connect with your website if those sources are blocked by the firewall due to being on the wrong side of the IP whitelist.
Additionally, since most businesses rely on external suppliers such as contractors and vendors who may need temporary access for certain tasks, using an overly restrictive whitelist could make managing all these different types of users difficult and time-consuming.
Conclusion
In summary, IP whitelisting is an important security tool that can help protect your data and systems from malicious actors while also helping you stay compliant with industry regulations like GDPR and HIPAA.
By creating a list of authorized “safe” IP addresses that have permission to access your system or website, you can ensure that only trusted individuals have access while keeping out anyone who shouldn’t be there. If you’re looking for an effective way to improve the security of your network environment, then consider implementing an IP whitelist today.